Click Hijacking Explained: The Hidden Threat Draining Your Ad Budget

What Is Click Hijacking?
Click hijacking is a deceptive and deeply damaging form of click fraud that siphons off your ad spend without you ever noticing. Unlike bots or click farms that inflate numbers with noise, hijackers intercept genuine user actions and redirect them for their own gain.
It’s stealthy. It’s smart. And it’s stealing from you.
If you're running PPC campaigns, mobile ads, or affiliate programmes, this silent threat could be inflating your performance metrics, stealing conversions, and wasting thousands in ad spend, all while your dashboards keep reporting “success.”
Protect your PPC campaigns with TrafficGuard’s click fraud detection software, built to identify and stop hijacked clicks before they waste your spend.
How It Works Behind the Scenes
Click hijacking works by tricking users into clicking on something they didn’t intend. A legitimate click, say, on a CTA or an ad, gets invisibly redirected. The user thinks they’re engaging with your site, but the interaction’s been hijacked.
This sleight of hand is typically executed through malicious code, hidden elements, or infected apps. The result? Fraudsters collect the credit, and your budget foots the bill.
Click Hijacking vs. Click Fraud: Key Differences
Let’s be clear: click hijacking is a form of click fraud, but it’s far more targeted.
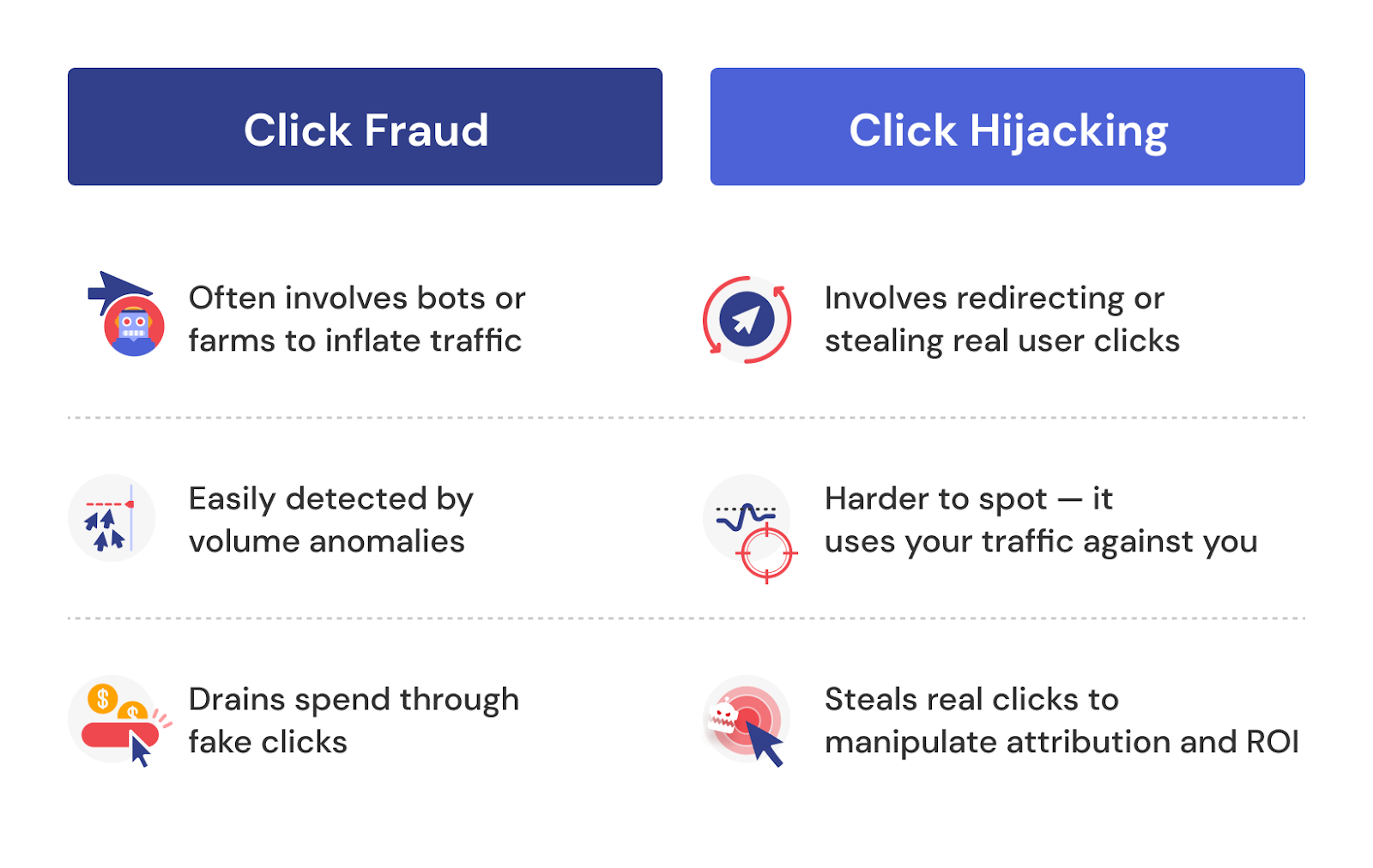
Click hijacking is click fraud evolved to become smarter, sneakier, and far more damaging to ROI.
Common Tactics Used in Click Hijacking
Hidden iframes and Invisible Buttons
One of the oldest tricks in the hijacker’s book. Fraudsters embed invisible elements on a page, like iframes or transparent buttons, that overlay real content. When a user clicks what they think is a legitimate element, the hijack is triggered.
Mobile App Hijacking Techniques
Mobile apps are fertile ground for hijackers. Some techniques include:
- Overlay attacks that trick users into clicking fake prompts
- Auto-redirects that launch malicious browsers
- Ad stacking, where multiple ads are layered and only one is visible
Mobile click hijacking is especially dangerous because it hijacks not just clicks, but installs and engagement, faking conversions and robbing you of valid attribution. Learn more about protecting your mobile app campaigns.
Affiliate Cookie Stuffing and Redirects
Affiliates looking to game the system often employ cookie stuffing, injecting hidden affiliate tracking cookies into a user’s browser without consent. That way, if the user eventually converts, they still get credit (and commission), even though they had nothing to do with the sale.
It’s attribution theft disguised as marketing. Learn how affiliate fraud prevention helps advertisers maintain fair and transparent partnerships.
Why Click Hijacking Is Dangerous for Advertisers
Budget Drain Without Awareness
Click hijacking burns through budgets quietly. You’ll see impressions, clicks, even conversions, but they’re not truly yours. The fraudsters cash in while you wonder why performance isn’t translating into revenue.
This is what makes click fraud protection so critical, because you can’t fix what you can’t see.
Attribution Theft and Fake ROI
Your campaigns might look like they’re performing well. But if clicks are hijacked, your data’s a lie.
Attribution models get corrupted, retargeting audiences get polluted, and you’re left optimising against false signals. It’s not just lost budget, it’s lost strategy.
Distorted Analytics and Conversion Data
Click fraud prevention software is only as good as its ability to detect behavioural anomalies. If hijacked clicks are flooding your funnels, your conversion data, bounce rates, and time-on-site metrics become useless.
You can’t make smart decisions if your foundation is fake.
Who Is Most at Risk from Click Hijacking?
Affiliate and Performance Marketers
Where there's incentive, there's exploitation. Affiliates working on CPA models are both targets and perpetrators of hijacking. Unscrupulous actors use it to claim unearned conversions, all while appearing as high-performers on paper.
Mobile App Advertisers
App installs and in-app events are easy hijack targets. Fraudsters manipulate install attribution using click injection and time-based redirects. If you’re not validating clicks and post-install behaviour, you’re exposed.
Brands Running Display or Programmatic Ads
If you're running display ads through programmatic platforms, hijackers can weaponise iframe abuse and redirect tactics to skim your clicks. And because it’s real traffic being redirected, it often flies under the radar of traditional fraud detection.
How to Detect and Prevent Click Hijacking
Behavioural Anomaly Detection
Start with the signals. Are you seeing high bounce rates from specific publishers? Conversions that don’t match typical user journeys? A surge in activity from one affiliate source?
These patterns are red flags. Smart click fraud prevention tools should flag them before the damage is done.
Using Real-Time Click Validation Tools
This is your frontline defence. Real-time click validation analyses traffic before it's paid for, identifying hijacked or manipulated clicks the moment they happen.
If your current setup doesn’t do this, you’re flying blind. TrafficGuard for Search uses real-time verification to prevent click fraud before your budget takes the hit.
Reviewing Traffic Sources and Attribution Patterns
Dig into referral traffic, UTMs, and post-click behaviour. Look for:
- Sudden spikes from low-quality sources
- Conversions clustered around a single affiliate ID
- Click-to-install times that defy logic
Fraud doesn’t hide from scrutiny, it hides behind neglect.
Final Thoughts: Taking Control Before It Costs You More
Click hijacking is not just another form of click fraud, it’s one of the most insidious. It distorts performance data, steals budget quietly, and undermines everything you think is working.
And the worst part? You often don’t know it’s happening.
That’s why marketers need to move from passive defence to proactive prevention. Don’t wait until your ROI flatlines or your analytics go haywire. Equip yourself with tools built to prevent click fraud, detect anomalies in real time, and protect the integrity of your marketing.
You deserve to know where your money’s going, and who’s really clicking.
FAQs & Key Takeaways
1. What exactly is click hijacking and how does it affect advertisers?
Click hijacking, often referred to as clickjacking, is a form of malicious manipulation where attackers trick users into clicking on hidden or disguised elements. The user believes they are interacting with a legitimate ad, CTA, or page element, but the click is silently redirected to a different target chosen by the fraudster.
For advertisers, the consequences are significant. Campaigns appear to receive high engagement, but none of that activity is intentional or valuable. Fraudsters steal attribution, capture conversions they did not influence, and drain ad budgets before marketers even realise anything is wrong. This kind of silent interception raises costs, damages reporting accuracy, and weakens optimisation strategies. TrafficGuard protects against this by validating every click and blocking hijacked activity in real time.
2. How does a clickjacking attack work in real user journeys?
A clickjacking attack works by placing transparent or disguised layers over a legitimate webpage or app interface. These layers can be invisible iframes, hidden JavaScript elements, or CSS-styled overlays. When a user clicks a visible button, the click is intercepted and directed somewhere else entirely.
In a real advertising journey, this could mean:
- A user clicks an ad believing it leads to a landing page, but is rerouted to a fraudulent affiliate link.
- A mobile user taps a confirmation button, but the tap is captured by an injected script that simulates an install or registration.
- A user scrolls and interacts with content, unaware that hidden elements are capturing interactions behind the scenes.
Because these attacks occur at the moment of interaction, most ad platforms cannot detect them. TrafficGuard monitors every click at the point of entry, inspecting technical signals, behaviour patterns, device environments, and redirect chains to identify and block hijacked interactions before they influence your campaigns.
3. What types of clickjacking attacks should marketers watch out for?
Marketers need to be aware of several forms of clickjacking that specifically target advertising and attribution systems:
- UI redress attacks: These disguise fraudulent actions behind legitimate UI components.
- Cursorjacking: The user’s cursor position is altered to cause accidental clicks on malicious content.
- Iframe overlays: Invisible frames capture clicks intended for real ads or CTAs.
- Likejacking or sharejacking: Tricks users into engaging with hidden social elements to inflate metrics.
- Mobile click injection: Fraudsters trigger fake clicks or app events milliseconds before a real user converts to steal attribution.
These attacks allow bad actors to claim conversions, inflate traffic numbers, and mislead optimisation engines. TrafficGuard addresses this risk by detecting behavioural irregularities, validating event sequences, and rejecting manipulated clicks before they enter your analytics pipeline.
4. What is the real impact of clickjacking on campaign data and ROI?
Clickjacking damages every layer of paid media performance. The most immediate impact is wasted budget on fraudulent clicks and manipulated conversions. However, the deeper and more dangerous impact is corrupted performance data.
Clickjacking causes:
- Inflated CTR and engagement metrics
- Artificially low conversion rates
- Distorted targeting signals
- Incorrect audience building and retargeting
- Misleading attribution paths
- Wasted optimisation cycles
Campaigns appear to work on the surface, but the underlying numbers are unreliable. This leads teams to scale the wrong channels, invest in underperforming audiences, and reduce spend on real users without realising the underlying issue. By blocking hijacked clicks and cleaning your traffic, TrafficGuard restores data accuracy so that teams can optimise with confidence.
5. How can marketers detect signs of click hijacking in their traffic?
Detecting click hijacking manually is difficult, but the signs often appear as unusual behavioural or technical patterns. Common indicators include:
- Very high click volume with no follow-through activity
- Clicks that fire too quickly to represent real user behaviour
- Suspicious referral URLs or traffic from unknown publishers
- Repeated conversions tied to the same affiliate or partner
- Abnormal click-to-install or click-to-conversion times
- Landing pages loading inside iframes when they should not
- Identical sessions where users take the same sequence of actions
The most reliable way to detect click hijacking is through continuous real-time validation. TrafficGuard identifies anomalies at the moment they occur, examining device attributes, click velocity, redirect behaviour, and engagement patterns to flag interactions that do not resemble genuine user activity.
6. What technical protections can stop clickjacking on websites and landing pages?
Website owners and marketers can defend against clickjacking using several technical security controls:
- Frame-busting headers: Use X Frame Options or Content Security Policy to prevent your pages from being embedded within iframes.
- Same-origin restrictions: Limit how external domains can interact with your content.
- Secure session handling: Ensure sensitive actions cannot be executed without explicit user interaction.
- Regular code audits: Check for injected scripts, unauthorised iframes, or suspicious external calls.
However, technical controls alone do not stop click hijacking in advertising. Attackers often target ranking pages, publisher inventory, affiliate networks, and mobile environments you do not control. This is why advertisers need a dedicated tool like TrafficGuard that validates every click from any source, across every channel, before it affects budget or data quality.
7. How can advertisers prevent clickjacking across PPC, affiliates, and mobile campaigns?
Preventing clickjacking requires a multi-layered approach that combines security practices with advanced validation:
- Validate each click before spend is committed.
- Monitor redirects and referral patterns for inconsistencies.
- Use behavioural analysis to differentiate real users from manipulated traffic.
- Audit affiliate partners for fraudulent behaviour.
- Review mobile app installs and events for signs of click injection.
- Track engagement depth rather than relying only on click metrics.
- Use real-time fraud prevention tools instead of manual reviews.
TrafficGuard supports all of these steps by providing continuous, automated monitoring. It verifies the intent, environment, and sequence behind every interaction, blocking hijacked clicks and protecting the accuracy of your performance data.
8. Which industries are most vulnerable to click hijacking and click injection?
Industries that rely on performance marketing and high-value conversions are the most heavily targeted. This includes:
- eCommerce: Fake clicks inflate top-of-funnel activity and damage ROAS.
- Betting and iGaming: High cost per acquisition models attract sophisticated injection attacks.
- Fintech and banking: Fraudsters exploit sign-up and onboarding funnels.
- Insurance: Lead generation campaigns are vulnerable to attribution theft.
- Telecom and subscription services: Subscription-related conversions are lucrative for fraudsters.
- Affiliate-driven businesses: Partners may use redirects or cookie stuffing to steal credit.
TrafficGuard helps these industries by validating clicks across search, social, display, mobile, and affiliate networks. This creates an environment where only real users, with real intent, are allowed into the funnel.
9. How does TrafficGuard stop click hijacking and protect ad spend?
TrafficGuard stops click hijacking by validating every interaction in real time. The platform analyses hundreds of behavioural, environmental, and technical signals, including:
- Device fingerprinting
- Redirect chain analysis
- Click velocity and frequency
- Session integrity
- Traffic source quality
- Historical behaviour patterns
- Engagement indicators
Suspicious or manipulated clicks are blocked before they can influence impressions, spend, or optimisation cycles. TrafficGuard also protects attribution pathways by verifying postbacks, install events, affiliate IDs, and conversion triggers. This allows advertisers to maintain data integrity and trust the performance numbers driving business decisions.
10. How much ad budget could click hijacking be costing me?
The financial impact varies by industry and campaign structure, but studies show that up to 22 percent of digital ad spend is lost to click fraud, with click hijacking responsible for a growing share of these losses. To estimate your potential exposure:
- Identify suspicious clicks, unusual engagement, or invalid activity.
- Calculate the percentage of traffic that does not lead anywhere meaningful.
- Apply your average conversion rate to estimate missed conversions.
- Multiply by your cost per acquisition or average order value.
For a fast estimate, use TrafficGuard’s Invalid Traffic Calculator. It gives a real-time indication of how much budget may be leaking from your campaigns due to click hijacking, click injection, and other invalid traffic threats.
Get started - it's free
You can set up a TrafficGuard account in minutes, so we’ll be protecting your campaigns before you can say ‘sky-high ROI’.
Explore More Blogs
Subscribe
Subscribe now to get all the latest news and insights on digital advertising, machine learning and ad fraud.








